Demystifying Differences: Penetration Testing vs. Vulnerability Scanning

Imagine the chaos, millions of customer records exposed, financial losses skyrocketing, and trust in tatters. This isn’t fiction; it’s the harsh reality of a cyberattack on an insurance company. In today’s data-driven world, where sensitive information resides in digital vaults, robust security is no longer an option, it’s an imperative.
But in the face of ever-evolving threats, how do insurance companies truly fortify their defenses? The answer lies in understanding two powerful security tools: penetration testing vs. vulnerability scanning. Though often confused, each plays a distinct role in safeguarding your sensitive data and customer trust.
This blog post delves into the intricacies of penetration testing (pentesting) and vulnerability scanning, demystifying their differences and highlighting their unique value in fortifying your insurance company’s security posture. By understanding the strengths and limitations of each approach, you can make informed decisions and build an impenetrable line of defense against cyber threats. So, buckle up, and let’s embark on a journey to crack the code of robust insurance security!
Table of Contents
Unmasking the Detectives: Penetration Testing vs. Vulnerability Scanning
Imagine your insurance company as a fortress protecting sensitive customer data. To ensure its security, you need two vigilant detectives: Vulnerability Scanning and Penetration Testing.
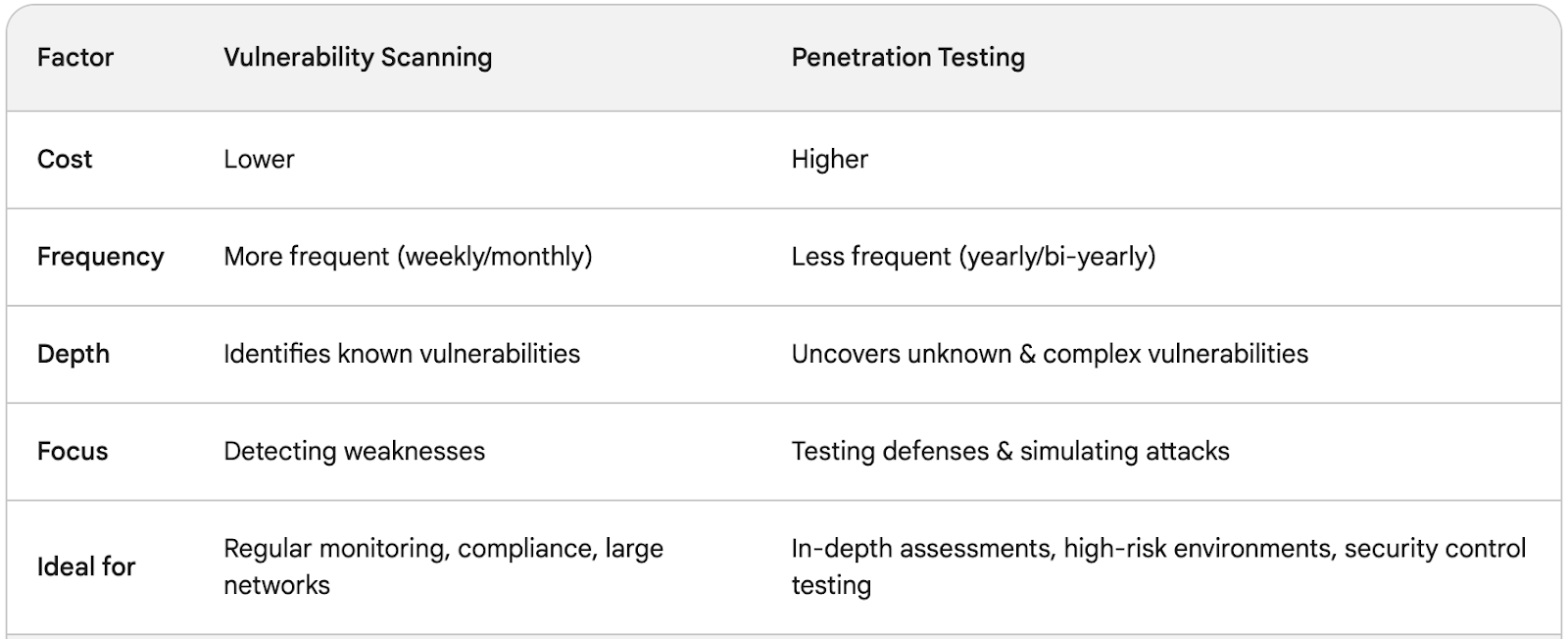
Vulnerability Scanning
This automated detective, like a high-tech fire alarm, continuously scans your systems for known weaknesses. It meticulously checks doors, windows, and firewalls, identifying vulnerabilities listed in its extensive database. If it finds a faulty lock (like an outdated software version), it raises the alarm, prompting you to patch the vulnerability before attackers exploit it. While efficient, this detective has limitations. Like a fire alarm, it can’t tell if a window is cracked open just slightly, or if a new, unknown vulnerability exists – gaps that cunning attackers might slip through.
Penetration Testing
This human detective, akin to a skilled security consultant conducting a fire drill, goes beyond alarms. They don the attacker’s hat, meticulously examining your defenses for any chinks in armor. They try picking locks (exploiting known vulnerabilities), but also scale the walls (identify zero-day vulnerabilities) and test even the most obscure entry points (complex system configurations). This hands-on approach uncovers not just known weaknesses, but also potential attack vectors you might have missed. While thorough, this detective requires more time and resources, similar to a comprehensive fire drill.
The Key Takeaway
Both detectives are crucial for robust insurance security. Vulnerability scanning provides constant vigilance, while pentesting offers in-depth assessments. Think of them as layers of protection: the alarm system and the security consultant working together to keep your digital fortress impregnable.
BPenetration Testing vs. Vulnerability Scanning: When to Choose Each Approach
Now that you’ve met our security sleuths, the question arises: who gets called when for maximum insurance security?
Vulnerability Scanning
Your go-to for regular checkups: Think of it as your monthly fire inspection. It’s cost-effective and identifies common vulnerabilities before they become critical breaches. Ideal for:
- Regular monitoring: Schedule scans weekly or monthly to stay ahead of evolving threats.
- Basic compliance requirements: Meets many industry and regulatory compliance standards.
- Large networks: Efficiently scans vast systems for known weaknesses.
Penetration Testing
For an in-depth security audit: Consider it a comprehensive fire drill, testing your defenses against real-world scenarios. Ideal for:
- High-risk environments: When protecting sensitive customer data, a deeper assessment is crucial.
- Testing security controls: Evaluates the effectiveness of implemented security measures.
- Preparing for sophisticated attacks: Uncovers complex vulnerabilities attackers might exploit.
Decision-Making Matrix
Remember: The best approach often combines both. Regular vulnerability scans provide a safety net, while periodic pentesting offers an in-depth audit, ensuring your insurance company remains a fortress against ever-evolving cyber threats. Don’t hesitate to consult security experts to design a tailored strategy that fits your specific needs and budget.
By strategically deploying these security detectives, you can crack the code of robust insurance security and safeguard your most valuable assets – customer trust and financial stability.
The Winning Hand: The Power of Combined Solutions
In the battle against cyber threats, a single line of defense is seldom enough. Just like relying solely on fire alarms wouldn’t guarantee your building’s safety, depending solely on vulnerability scanning or pentesting leaves gaps in your insurance security posture.
The winning hand lies in combining both approaches. This is where Vonahi Security and our comprehensive security solutions come into play.
Introducing a Powerful Partnership
We proudly partner with Vonahi Security, a leading provider of automated vulnerability scanning solutions. This powerful combination allows us to offer you a seamless package that encompasses:
- Automated Vulnerability Scanning: Vonahi’s advanced tools continuously scan your systems, identifying known vulnerabilities with unmatched efficiency. Think of it as an ever-vigilant fire alarm system, constantly monitoring for potential threats.
- Expert Penetration Testing: Our team of seasoned security professionals, certified ethical hackers, conduct in-depth pentesting, simulating real-world attack scenarios. They go beyond alarms, meticulously examining your defenses for even the most obscure vulnerabilities, acting as your skilled security consultants conducting comprehensive fire drills.
Double the Expertise, Double the Protection
Our team boasts extensive experience in both vulnerability scanning and penetration testing. We hold industry-recognized certifications and actively participate in cybersecurity communities, ensuring we stay ahead of the ever-evolving threat landscape. This expertise translates into:
- Accurate vulnerability identification: We leverage Vonahi’s superior scanning technology to pinpoint every known weakness in your systems.
- Uncovering hidden threats: Our pentesting goes beyond the surface, meticulously testing your defenses and uncovering even zero-day vulnerabilities before attackers exploit them.
- Actionable insights & remediation plans: We don’t just identify vulnerabilities; we provide clear, actionable recommendations and support you in implementing effective remediation strategies.
By combining Vonahi’s automated scanning with our expert pentesting, we create a security shield that’s both comprehensive and cost-effective. We empower you to proactively identify and address vulnerabilities before they turn into costly breaches, safeguarding your sensitive data and customer trust.
Fortify Your Fortress: Take Action Today!
The choice is clear: in today’s digital landscape, robust insurance security demands a multi-layered approach. By combining the relentless vigilance of vulnerability scanning with the in-depth analysis of penetration testing, you can create an impenetrable shield against cyber threats.
Don’t wait for a breach to expose your vulnerabilities. Take action today and empower your insurance company with the winning hand. Call 212-255-3970 and ask for Michael or Richard to discuss a PenTest solution tailored to your specific needs and budget.
Our team of experts is eager to partner with you in crafting a comprehensive security strategy that safeguards your most valuable assets – customer trust and financial stability.
Remember, prevention is always cheaper than the cure. Act now and build a fortress to withstand the storm of cyber threats.
We look forward to hearing from you!
Frequently Asked Questions
What’s the Key Difference Between Vulnerability Scanning and Penetration Testing?
Vulnerability scanning is automated, identifying known weaknesses like a security alarm. Penetration testing is manual, simulating real attacks to uncover both known and unknown vulnerabilities, like a security consultant actively trying to break in.
Why Might Pen Testing Seem “Better” Than Scanning?
Pen testing offers a deeper analysis, but it’s not a replacement. Scanning provides continuous monitoring, while pen testing offers in-depth audits. The best approach combines both for optimal security.
What are the 4 Main Types of Vulnerabilities?
1. Injection vulnerabilities: Malicious code inserted in user inputs (e.g., SQL injection, XSS).
2. Broken authentication/authorization: Weak passwords, lack of multi-factor authentication, or improper access controls.
3. Misconfiguration vulnerabilities: Incorrectly configured systems or applications.
4. Zero-day vulnerabilities: Previously unknown vulnerabilities exploited before a patch exists.